The one thing that is always constant in life is change. The climate of the physical security industry is no different. We asked Security Consultant, Pierre Bourgeix, what he sees as “out” in 2018 and “in” in 2019 based on his conversations with clients and his close involvement in the industry.
As you start thinking about your 2019 physical security plan, examine whether or not your organization is keeping up with the changes. Keep scrolling to read about each of the "outs" and "ins" in more detail.
 Security Practices
Security Practices
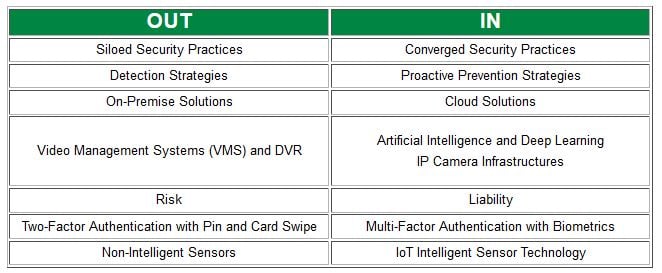
OUT: Siloed Security Practices
Most organizations have always worked in a siloed environment, making decisions in a bubble without interaction from other business units or specifically practices such as Information Technology (IT), Operational Technology (OT) and Physical Security (PS).
IN: Converged Security Practices
As technology becomes more connected by network infrastructure, the domains of IT, OT, and PS can no longer be siloed and decisions can’t be made in a bubble. This leads to a more converged decision-making process as well as governance around business processes and security (from cyber to physical).
To learn more about Converged Security Practices, read an article published by SecurityInformed.com.
Detection vs. Prevention Strategies
OUT: Detection Strategies
For the past 50 years, the security industry has been in a detection mode, implementing burglar alarms, guard services and video cameras to mitigate infiltration. This approach has its weaknesses though, as these security measures can be circumvented – guards get distracted, alarms sound only after the intruder is already inside, cameras record the incident as its happening. All of these measures are reactive in nature.
IN: Proactive Prevention Strategies
With the increase of active shooter events and workplace violence, merely responding to an event is no longer acceptable. As a result, most organizations that are dealing with threats and vulnerabilities are looking to new prevention strategies that stop an incident from escalating in the first place. These measures include the use of biometrics and multi-factor authentication, as well as a shift from the use of strictly turnstile solutions to security revolving doors and mantrap portals. Proactive prevention is necessary for highly compliant environments.
Location of Security Solutions
OUT: On-Premise Solutions
Most organizations manage their physical security on-premises, where a guard or manager is inside the physical building, monitoring cameras, DVR, burglar alarms, guards and access control systems.
IN: Cloud Security Solutions
There has been a significant increase in cloud-based solutions as part of the security infrastructure. This set-up allows organizations to access solutions, such as cloud video and access control, remotely. With the proliferation of IoT (Internet of Things), we also see interconnectivity of devices across national and international companies, allowing them to link and manage devices in an enterprise environment.
Video Management Evolution
OUT: Video Management Systems (VMS) and DVR
Video has been predominantly used as a forensics tool. Typically, organizations link cameras to a VMS and a DVR for security management. This has limitations, though – storage, difficult to scale, not easy to detect an event. Sadly, there have been serious events, like theft and safety violations, that weren’t recognized on video until 30-60 days afterwards. With the birth of more advanced IP cameras, this shift from analog to more intelligent solutions is a reality.
IN: Artificial Intelligence (AI), Deep Learning and IP Camera Infrastructure
There has been a significant rise in the use of analytics within the video management industry. The shift from analog to IP cameras and network cloud-driven infrastructure has given companies the ability to develop unified systems that can pull metadata, stream video, and provide alerts. This allows deep learning and AI to create metrics and tendencies that are tracked over time. With secured storage and communication, we see a world that is truly connected and secure.
Risk and Liability
OUT: Risk
The term “risk” is associated with potential loss. And, with the growth of intelligent technology, risk has grown exponentially. However, risk is often easily pushed aside by the C-suite. Why? Because organizations think, “It won’t happen to me.” Risk can be pushed away or negotiated.
IN: Liability
Risk without measurement can and will be denied by the C-suite. However, liability, which is attached to compliance, legal, business ethics and governance is less likely to be pushed away. Liability is defined by metrics and these facts are absolute. With the use of technology, deep learning, and analytics across IT, OT, Physical Security and IoT, we will see the growth of true results that lead to acceptance by those in decision-making power.
Identity
OUT: Two-Factor Authentication with Pin and Card Swipe
The expansion of technology within the access control industry and the need for true identity verification at the entry has led to the need for validation methods that go beyond the traditional two-factor authentication method with Pin and Swipe. This outdated method also leaves an organization open to potential liability connected with compliance.
IN: Multi-Factor Authentication with Biometrics
The growing trend in the market is to implement a multi-factor authentication identity process with biometric devices. The ability to authorize users based on unique biological traits provides an organization with a higher, stronger level of protection against unauthorized entry. And, through use of this method of access, organizations are achieving the goal that ICAM (Identity, Credential and Access Management) sought out to achieve over 10 years ago. ICAM provides enterprise-class services that assist in managing digital identities, credentials, and access to systems and applications. Multiple biometric authorizations for entry has been a nice-to-have, but will soon become a need-to-have.
Smart Devices
OUT: Non-Intelligent sensors
As the world embraces the growth of Smart Buildings and Smart Cities, we are seeing an increase in the number of devices and sensors that are automating our lives - opening doors and gates, turning on televisions, starting cars, the list goes on. However convenient, these devices are also becoming the vehicle hackers use to breach the network environment of an organization. In 2019, we will see the market ask for intelligent and secure sensors and IoT devices.
IN: IoT Intelligent Sensor Technology
The use of IoT devices will be in the billions by 2020. The key to integrating these into a successful security plan is ensuring communication paths and the infrastructure are protected against threats and vulnerabilities. With more intelligent sensor technology capable of collecting data and providing metrics, we will begin to see an interconnection between the IT, OT and Physical Security environments, as well as stronger physical and cyber controls in place to protect against a potential breach.